
My dude, I am positive. My cake day: June 8 2023. Your cake day: June 12, 2023. Do you not realize that people can have multiple accounts? Dick measuring and attempts at gate keeping based on time on a platform is super cringe.
I created the community you’re posting in right now. You should probably get off the internet and chill bro. You woke up and made the choice to behave this way, and it’s pretty fucking embarrassing tbh.
Ah, like just set up a guest account for each instance i’m interested in, then browse by local for each one?
That sounds like a potential workaround, but unless i’m missing something I’m still subject to only seeing the communities that are hitting the feed based on whichever sorting algorithm I’m using right? It seems like adding something like“view all communities by instance” tab to the app search page then using similar logic to that in the instance selection field on the signup page would be more useful and useable as a user to me personally.
I obviously pulled a lot from Apollo into Arctic, which if in being honest, I feel a little guilty about.
Sorry to respond to such an old post, but I wouldn't feel guilty about this. Christian said he absolutely did not want to convert Apollo to Lemmy, and that he was done with the project. I'm really glad that you've made an app that feels so familiar and comfortable for me coming from Apollo, I wouldn't use Lemmy nearly as frequently without your app.
While browsing through the 'All' subscription feed I'll occasionally see a post from an instance that looks interesting to me, for example programming.dev, and I would like to browse the communities that are hosted on that instance.
The search functionality within the app only allows for me to find communities with programming.dev in the community name. Currently I have to navigate to the instance directly in a browser using the httx://*/communities?listingType=Local endpoint to view all its local communities.
Even if incorporating such a view is a possibility I'm not sure where you would integrate it in to the UI. Maybe an Instance sub-menu with a nested Local Communities menu item underneath the existing Community menu item in the ... Options menu at the top of the screen while viewing a post?
On a semi-related note, would it be possible to add an option to view the community sidebar while viewing a post and its comments? I currently have to scroll up to the top of the post, click on the link to follow though to the community directly, then open the sidebar from the Options menu there.
That’s been my life for the past 10 years, you won’t regret it at all.
And leaded gasoline and leaded diesel and leaded aviation fuel and lead pipes in household plumbing. Probably lead in the cigarettes everyone smoked literally everywhere.
Saying they banned VPNs isn’t completely, technically correct I’d guess. If I were another country then VPN’d in to my house, I would probably be fine. A pedantically correct statement would be that they banned known VPN IP ranges, so if you’re attempting to connect while your traffic is routed through one you get blocked.
Oh damn. Yeah fuck that place, glad I left.
Semi-related, I was searching for some hyper specific job related technical cybersecurity stuff a few weeks ago and the first result with the verbatim error message was a reddit post, so i clicked. No dice, loads a reddit branded error page. My employer has their own ARIN number/ASN. As far as i could tell every connection from an IP in one of our blocks was being blocked by reddit. My employer isn’t a faang type tech company, they don’t work in ai, they don’t scrape content for datasets or anything else. I can’t figure out why kind of business would cut off entire swaths of customers from accessing their site during the workday, a prime “take a shit and dick around on the phone” audience. I’ve just made a point to search with stack exchange site dorks since then.
We got 4 mainline games in the first 18 years, which works out to a game every 4.5 years on average. We have been getting ports and remasters of a single game for the remaining 12 years. Idk what happened over there. Did the main TES devs just burn out? If so why all the ports and rereleases? Maybe they’re just sticking a revolving door of interns on those?
Edit - Oh I guess the TES mmo. Still though.
Absolutely filthy prodigy remix in the first video. Gotta love the russian at 1:15 looking like he’s trying to get a rewind for that drop but really just can’t move his leg or floppy foot lol.
Yeah, the answer here is cancel prime and pirate whatever amazon video content you want. if you absolutely have to have prime for some reason, don’t sign in to amazon video on any of your devices and pirate the stuff you want to watch so at least your not contributing to views or their prime video ad revenue.
Edit - I see in another comment you said you unsubscribed, good on you.
I’m slightly less mad now that I know this has precedent. I’m still fucking furious that the only precedent I’ve heard about is corporations and Trump, since the law should be equally applied regardless of absolute amounts of money and I’m pretty sure that someone living in poverty isn’t going to get the same treatment for a $50k (or whatever is a proportional amount) judgement against them.
That wasn’t what was at stake here. Trump was already found guilty, he wasn’t bonding out of pretrial detention he was having to post bond in order to appeal the ruling, which typically requires the person making the appeal to post a bind to make sure they don’t spend all their money fighting on appeal, just to lose the appeal and not have any money left to pay the original judgement.
So my expectation was that yes, he would have to follow the same court rules as everyone else and put up the bond in order to appeal. While I do think we should get rid of requiring pretrial detention bond, I don’t necessarily see an issue with requiring pre-appeal bond. I don’t know, you don’t want to create a situation where you’re means testing the right to appeal, but you don’t want people to indefinitely delay enforcement of judgement against them or to allow them to spend away their ability to pay the judgement on appeals. Maybe forcing either the entirety of the judgement to be paid into a more traditional escrow account, or a payment plan for the judgement to be accepted and that paid into escrow, before an appeal can be started?
Any way you cut it though, I can’t fault this chuckle fuck for playing the court game but I’m fucking incensed the court is enabling it.
I’ve replaced the pads on mine a couple times, the rubber on the thumb rest has a hole worn it it to the plastic, and the braided cable is all frayed and stuff. I’ve had the thing for the past 10 years at least. I know new ones are that cheap and that I should just get a new one at this point but the thing is just a workhorse.
It is part of the deep web, just like Discord or any sites hosted on private companies intranets. Lemmy is not, you can just hit any instance with a web browser and view stuff.
To be completely clear, dark web/net and deep web are two different things. That wiki link you used is describing dark web stuff like tor etc.
How the fuck both the prime ministers from 2013 mentioned in that wiki article still leading their respective countries 11 years later?
No Crocus skin? 2/10, gonna buy another crate and key.
Oh damn, I’m gonna have to find that shit. I am regularly shocked at how hard CBS Saturday/Sunday Morning goes though, they will throw some savage shit on the air for the grandmas watching human interest stories about Broadway actors and whatever the fuck Mo Rocca has gotten interested in recently.
Edit - Found it on a Ukrainian dead Russian combat footage telegram. Bit rate is garbo but it looks like even ISIL is full sending the whole weeb CS gun skin thing lol. Best part is the posts of air raid sirens and distant explosions from Belgorod, with the caption “Помста за вухо таджика”.
Ah ok, I misinterpreted your post then. I thought you were insinuating that because refineries are civilian infrastructure Ukraine shouldn’t be targeting them. We’re in agreement here, don’t target actual civilians and slam as many drones as possible into refineries and any other valid targets within Russia.
detailing that he had been promised 500,000 rubles ($5,418).
Fuck me, this really hammers home that first world privilege. More than that amount of USD hits my checking account each month in my direct wages. This guy knew what would happen to him when he was caught then decided that risking misery in Siberia before being executed was worth less than a month of my take home pay. I mean i get that some level of radicalization is involved here, but still what the fuck.
The distinction is not between civilian targets and military targets, it is between “civilian objects” and “military objectives”. Targeting a civilian infrastructure such as refineries, and even civilian power stations can be considered valid military objectives if they make an effective contribution to military action or offer a definite military advantage. The refineries being hit by Ukraine definitely meet that definition.
https://www.reuters.com/world/europe/when-are-attacks-civilian-infrastructure-war-crimes-2022-12-16/
At the beginning of this year, we released a detailed publication on Vidar infrastructure, encompassing both the primary administrative aspects, and the underlying backend. In that publication, we highlighted three key insights: Russian VPN gateways had the potential to confer anonymity to Vidar ope...

Team Cymru published a report detailing infrastructure and configuration changes to the Vidar info-stealer malware that were made in an attempt to evade detection and anonymize activities.
ESET researchers analyzed an updated version of Android GravityRAT spyware that steals WhatsApp backup files and can receive commands to delete files.

ESET researchers identified an updated version of the Android GravityRAT spyware being distributed as the messaging apps BingeChat and Chatico.
Without altering a single line of code, attackers poisoned the NPM package “bignum” by hijacking the S3 bucket serving binaries necessary for its function and replacing them with malicious ones

It seems like attackers have discovered a way to leverage NPM packages to deliver malicious binaries without needing to make any changes to the NPM package itself.
Attackers heavily focused on acquiring military and security intelligence in order to support invading forces.

This is an interesting report by Symantec about a Russian 'Cyber Campaign' against Ukraine, targeting security services, military, and government organizations.
It's crazy that we're witness to the first case in history of cyber warfare campaigns being waged alongside, and in support of, a hot war, in real time.
Looks like Mandiant has discovered active exploitation of CVE-2023-20867, which was given a CVSS score of 3.9 when it was assigned.
In May 2023, the Trellix Advanced Research Center discovered a new Golang stealer, known as Skuld, that compromised systems worldwide. The malware targets sensitive information stored in certain applications, such as Discord and web browsers, and the Windows system. The author, Deathined, has taken ...

This new malware strain, written in Go, has been seen compromising systems across Europe, Southeast Asia, an the U.S. It's stealing sensitive information from Discord, web browsers, etc.
Several fake researcher GitHub accounts are pushing malicious code, claiming to exploit zero-day flaws in Discord, Google Chrome.
This won't apply to anyone here, because we're all reviewing any code we clone from GitHub prior to executing it on our system, right?
Using a variety of CTI enrichment techniques Sygnia was able to determine that the BEC attack was only a part of a much wider campaign, potentially impacting dozens of world-wide organizations.

Kaspersky researchers share insight into multistage DoubleFinger loader attack delivering GreetingGhoul cryptocurrency stealer and Remcos RAT.

This new stealer has five stages, and shows a high level of sophistication, akin to APTs. Targeted victims have been seen in Europe, the USA, and Latin America.
Several pieces of Russian text were found in the malware. > The first part of the C2 URL is “Privetsvoyu” which is a misspelled transliteration of the Russian word for “Greetings.” Secondly, we found the string “salamvsembratyamyazadehayustutlokeretodlyagadovveubilinashusferu.” Despite the weird transliteration, it roughly translates to: “Greetings to all brothers, I’m suffocating here, locker is for bastards, you’ve messed up our area of interest.”
MD5 sum and C2 URL IOCs are included at the end of the report.
A vulnerable password reset API made it possible to take over any account and gain admin-level access to the platform. In addition, broken/missing access controls made it possible to access all data on the platform.

The researcher chained an insecure password reset API route to bypass authentication, then discovered an IDOR vulnerability could be leveraged to access sensitive customer data.
For everyone that says "The real world can't be as easy as training labs make it seem out to be!", sometime it really do be that ez.
Urgent: A new critical RCE security vulnerability in FortiGate firewalls has been discovered.

Fortigate published a patch for CVE-2023-27997, a Remote Code Execution vulnerability reachable pre-authentication, on every SSL VPN appliance.
I thought I'd take a break from posting stories that come across my RSS feed to let people know about an upcoming Hack-A-Thon/CTF event that OffSec is running next weekend.
I'm not really sure what the challenges will entail, since I'm not eligible for any of the prizes I haven't been paying much attention to info about it at all. I do know that in order to compete you will have to have an active PG Practice subscription, which is $19 USD/mo, more info is here. I don't really like that they're requiring people to already have a paid subscription to compete, but it's their ecosystem and their rules.
There are three different tiers you can compete in, a PEN-300 tier, an EXP-301 tier, and an PEN-200 tier. The 1st prize for each tier is a year long LearnOne subscription to the tier course, 2nd place is a 90 day course subscription to the tier course, and 3rd place is a 90 day subscription to the PG Practice environment.
While SANS is the king of wildly expensive courses, the OffSec subscriptions definitely aren't cheap either, especially if you're self-paying. I get the irony of making people pay for entry into a contest where they might win a subscription they otherwise couldn't afford, but it's better than nothing I guess.
Elastic Security Labs has discovered the P8LOADER, POWERSEAL, and SPECTRALVIPER malware families targeting a national Vietnamese agribusiness. REF2754 shares malware and motivational elements of the REF4322 and APT32 activity groups.

Elastic Security Labs has discovered the SPECTRALVIPER malware targeting a national Vietnamese agribusiness.
Attention all businesses using MOVEit Transfer! Progress Software has just rolled out critical patches to address new SQL injection flaws.

Looks like a patch was released yesterday for the SQL injection vulnerabilities discovered in the MOVEit Transfer application.
The direct link to the official announcement is here.
Hello and welcome! I joined the Lemmy fediverse a week ago, and settled in to the sh.itjust.works instance yesterday. I had pulled back from most of my social and general use of Reddit a few years back, and mostly just used it as a more social RSS feed to keep abreast of things going on in the cybersecurity and information security world. One of the first things I noticed when exploring the Lemmy Fediverse was that outside of the general tech communities, there was only a single cybersecurity community which hadn't seen any activity in over a year or more.
I've gone back to my old stalwart RSS feeds, so I decided to create this community and post any articles I find interesting that come across my feed. Hopefully others will find it helpful as well!
I really hope that the social aspect of the community will take hold here too, and encourage anyone to make any link or text posts related to cybersecurity that they want. I don't really want this to turn into a place where every other question is "How do I get into cybersecurity?" or "Will you be my mentor?", but the Lemmy community is small so at this point I'd welcome any sort of community interaction.
To kick things off with a little about myself, started my career working as a network engineer for a WISP, scampering across city roofs, throwing up non-pen mounts for PtP radios, and slinging multi-Gbps links from building to building. I slowly transitioned into a SOC through a few calculated job transitions, then after a few more I've found myself working on a team that splits our time providing penetration tests for internal business lines and running red team/adversary emulation engagements against my company. Over the past few years I've earned my OSCP, OSEP, and OSWE, along with a handful of GIAC certifications. I'm currently working on the study materials for the OSED. I don't have any coding experience, just a bit of scripting ability, but I am very excited to jump in to binary exploitation and reverse engineering. It's the closest thing to magic to me in this space, and I can't wait to deconstruct and demystify it a bit.
Thanks for reading, and glad you're here!
Microsoft Defender Experts observed a multi-stage adversary-in-the-middle (AiTM) and business email compromise (BEC) attack targeting banking and financial services organizations over two days. This attack originated from a compromised trusted vendor, involved AiTM and BEC attacks across multiple su...
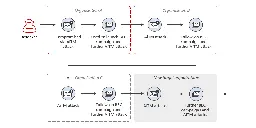
Microsoft researchers have discovered an emerging cluster of TTP's they have named Storm-1167 being used by an unknown threat actor to target banking and financial services institutions.
This threat actor has been utilizing phishing emails for initial compromise, then using compromised inboxes to further distribute their malicious phishing emails.
The threat actor has been observed taking steps to minimize detection and to establish persistence.
ESET released an analysis of the Asylum Ambuscade crimeware group that has been active since at least early 2020.
This group targets bank customers and cryptocurrency traders in regions including North America and Europe.
The TTP's related to initial access include spearphising emails containing malicious XLS and DOC files.
ChatGPT’s fabrications are starting to catch up with OpenAI

 borari @sh.itjust.works
borari @sh.itjust.works Cybersecurity professional with an interest in networking, and beginning to delve into binary exploitation and reverse engineering.

