Encryption
- The Linux Foundation and its partners are working on cryptography for the post-quantum worldwww.zdnet.com The Linux Foundation and its partners are working on cryptography for the post-quantum world
Quantum computing is very much a mixed blessing.

cross-posted from: https://links.hackliberty.org/post/989486
> We know the end of the line is in sight for classical cryptography. All the security encryption that protects our bank accounts, websites, and credit cards today will eventually be broken. That's not just a threat; that's the reality. > > When Q-Day comes, which is the day quantum computers can break our existing encryption methods, we'll need a replacement for Advanced Encryption Standard (AES), RSA, and Blowfish. That's why the Linux Foundation and others have united behind the Post-Quantum Cryptography Alliance (PQCA). > > It's also important to note that Bitcoin and other cryptocurrencies will be broken, too. As the Katten law firm's Daniel Davis and Alexander Kim recently observed: "Quantum computers have the potential to break the most advanced cryptographic protocols -- including those used for blockchain protocols -- in operation today." > > PQCA is meant to galvanize the development and widespread adoption of post-quantum cryptography. These new crypto algorithms will be able to resist quantum computers' efforts to break them. PQCA is a collaborative platform, uniting the brightest minds from industry giants, academia, and the developer community to tackle the cryptographic challenges of the quantum age. > > Leading the charge are founding members, such as tech behemoths Amazon Web Services (AWS), Cisco, Google, and IBM. Their collective expertise and resources are poised to propel the PQCA's mission to secure sensitive data and communication in the post-quantum world. > > Jim Zemlin, the Linux Foundation's executive director, said: "By establishing an open and collaborative environment for innovation, the PQCA will help accelerate the development and adoption of post-quantum cryptography in open source and beyond." > > Yet the great minds in PCQA aren't the only experts focused on this crucial area. The National Institute of Standards and Technology (NIST) is already working on four quantum-proof crypto algorithms: > > - CRYSTALS-Kyber is designed for general encryption purposes, such as creating secure websites. > > - CRYSTALS-Dilithium is designed to protect the digital signatures we use when signing documents remotely. > > - SPHINCS+ is also designed for digital signatures. > > - FALCON is another, less mature, algorithm for digital signatures. > > The work from PQCA will be the central foundation for organizations and open-source projects seeking production-ready libraries and packages to support these quantum-proof algorithms and the U.S. National Security Agency's Cybersecurity Advisory concerning the Commercial National Security Algorithm Suite 2.0. > > Part of PQCA's mission is its commitment to the practical application of post-quantum cryptography. The alliance will spearhead technical projects, such as developing software for evaluating, prototyping, and deploying new post-quantum algorithms. In other words, the alliance seeks to bridge the gap between theoretical cryptography and its real-world implementation. > > One of PQCA's launch projects is the Open Quantum Safe project, which was founded at the University of Waterloo in 2014 and is one of the world's leading open-source software initiatives devoted to post-quantum cryptography. > > PQCA will also host the new PQ Code Package Project, which will build high-assurance, production-ready software implementations of forthcoming post-quantum cryptography standards, starting with the ML-KEM algorithm. > > All this effort matters because quantum computing is very much a mixed blessing. As Jon Felten, Cisco Systems' senior director of trustworthy technologies, said: "Quantum computing offers the potential to solve previously unapproachable problems, while simultaneously threatening many digital protections we take for granted." > > This "transition to Quantum-Resistant standards, algorithms, and protocols will undoubtedly be a challenging one," said Ted Shorter, CTO of Keyfactor. What's already clear is that we're entering a new era of computing. We won't know how effective our preparations will be until quantum computers have enough qubits to crack our existing encrypted data. > > The level of progress is such that IBM recently released the first 1,000-qubit chip. That level of performance isn't enough to reach Q-Day. However, it's a moment that isn't too far from being realized.
- Mathematician warns US spies may be weakening next-gen encryptionweb.archive.org Mathematician warns US spies may be weakening next-gen encryption
Quantum computers may soon be able to crack encryption methods in use today, so plans are already under way to replace them with new, secure algorithms. Now it seems the US National Security Agency may be undermining that process

Daniel Bernstein at the University of Illinois Chicago says that the US National Institute of Standards and Technology (NIST) is deliberately obscuring the level of involvement the US National Security Agency (NSA) has in developing new encryption standards for “post-quantum cryptography” (PQC). He also believes that NIST has made errors – either accidental or deliberate – in calculations describing the security of the new standards. NIST denies the claims.
“NIST isn’t following procedures designed to stop NSA from weakening PQC,” says Bernstein. “People choosing cryptographic standards should be transparently and verifiably following clear public rules so that we don’t need to worry about their motivations. NIST promised transparency and then claimed it had shown all its work, but that claim simply isn’t true.”
The mathematical problems we use to protect data are practically impossible for even the largest supercomputers to crack today. But when quantum computers become reliable and powerful enough, they will be able to break them in moments.
Although it is unclear when such computers will emerge, NIST has been running a project since 2012 to standardise a new generation of algorithms that resist their attacks. Bernstein, who coined the term post-quantum cryptography in 2003 to refer to these kinds of algorithms, says the NSA is actively engaged in putting secret weaknesses into new encryption standards that will allow them to be more easily cracked with the right knowledge. NIST’s standards are used globally, so flaws could have a large impact.
Bernstein alleges that NIST’s calculations for one of the upcoming PQC standards, Kyber512, are “glaringly wrong”, making it appear more secure than it really is. He says that NIST multiplied two numbers together when it would have been more correct to add them, resulting in an artificially high assessment of Kyber512’s robustness to attack.
- Is there any security in scrambling bits?
Like, could you just invert all the bits in a block of data and turn it into nonsense?
Or shift/rotate bits, so 10000101 would become 00001011, rather than using an encryption function.
It would be easy to break if you just figured out which bit operations were made, but it's a wierd thing to do so.. would it be obvious at all that it was such a simple encryption method from the raw data?
Just had that thought, it sounds like a 'security through obscurity' measure.
- ECH is Going Mainstream, and it Could Help Liberate Blocked Websitesreclaimthenet.org ECH is Going Mainstream, and it Could Help Liberate Blocked Websites
Join Reclaim The Net.

The war against online censorship and surveillance recently saw a formidable development that could turn the tide in favor of internet freedom and privacy. Cloudflare, the notable internet infrastructure titan, has unveiled support for the Encrypted Client Hello (ECH) privacy feature, essentially creating a sanctuary for free speech advocates and challenging established site-blocking endeavors.
For the uninitiated, as TorrentFreak reported, web blocking has been the entertainment sector’s favored anti-piracy tool for over a decade and a half. Employed in more than forty nations, this method involves Internet Service Providers (ISPs) blocking access to specific websites, often under a legal directive. While it started with rudimentary DNS blockades, the system evolved, employing sophisticated Server Name Indication (SNI) eavesdropping techniques, or sometimes a mix. But it has also been used as a way for governments to censor websites and block access.
However, the landscape began shifting as privacy-centric technologies, like Encrypted DNS, emerged to challenge these blockades. Now, the introduction of ECH is poised to revolutionize this arena, making ISP’s surveillance efforts mostly, if not entirely, ineffective.
Described simplistically, ECH is an innovative privacy protocol engineered to mask internet traffic, thwarting any monitoring efforts. Browser giants like Chrome, Firefox, and Edge have already given a nod to its implementation. Yet, for its potential to be fully realized, websites must also incorporate it. Cloudflare’s decision to eventually integrate ECH by default in all its free plans, serving countless websites, signifies a giant stride towards widespread adoption.
- Quantum Resistance and the Signal Protocolsignal.org Quantum Resistance and the Signal Protocol
The Signal Protocol is a set of cryptographic specifications that provides end-to-end encryption for private communications exchanged daily by billions of people around the world. After its publication in 2013, the Signal Protocol was adopted not only by Signal but well beyond. Technical informat...
The Signal Protocol is a set of cryptographic specifications that provides end-to-end encryption for private communications exchanged daily by billions of people around the world. After its publication in 2013, the Signal Protocol was adopted not only by Signal but well beyond. Technical information on the Signal Protocol can be found in the specifications section of our docs site.
Today we are happy to announce the first step in advancing quantum resistance for the Signal Protocol: an upgrade to the X3DH specification which we are calling PQXDH. With this upgrade, we are adding a layer of protection against the threat of a quantum computer being built in the future that is powerful enough to break current encryption standards.
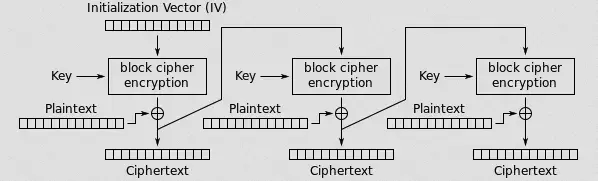
- AES: How to Design Secure Encryption (Spanning Tree)
In 1997, a contest began to develop a new encryption algorithm to become the Advanced Encryption Standard. After years of debate, one algorithm was chosen as the AES. But how does AES work? And what makes for a secure encryption algorithm?
***
Spanning Tree is an educational video series about computer science and mathematics. See more at https://spanningtree.me
To be notified when a new video is released, sign up for the Spanning Tree mailing list at https://spanningtree.substack.com/
Spanning Tree is created by Brian Yu. https://brianyu.me/
Email me at brian@spanningtree.me to suggest a future topic.
***
- 0:00 The Contest
- 1:02 Encryption
- 3:57 Confusion and Diffusion
- 5:44 Block Cipher
- 6:55 KeyExpansion
- 7:34 AddRoundKey
- 8:14 Substitution Cipher
- 8:55 SubBytes
- 11:30 MixColumns
- 12:53 ShiftRows
- 13:21 The Algorithm
---
- https://www.youtube.com/watch?v=C4ATDMIz5wc
- https://piped.video/watch?v=C4ATDMIz5wc
Aug 22, 2023
- Help users in Iran reconnect to Signalsignal.org Help users in Iran reconnect to Signal
Just over a week ago, we announced that Iranian censors had started blocking all Signal traffic in the country. As an interim solution to help people in Iran get connected again, we’ve added support in Signal for a simple TLS proxy that is easy to set up, can be used to bypass the network block, ...

cross-posted from: https://community.hackliberty.org/post/4425
>"Just over a week ago, we announced that Iranian censors had started blocking all Signal traffic in the country. As an interim solution to help people in Iran get connected again, we’ve added support in Signal for a simple TLS proxy that is easy to set up, can be used to bypass the network block, and will securely route traffic to the Signal service."
- Tornado Cash Code Repositoriesgithub.com tornado-repositories
tornado-repositories has 34 repositories available. Follow their code on GitHub.

cross-posted from: https://community.hackliberty.org/post/2113
These repositories contain an archival fork of the Tornado Cash and Tornado Cash Nova source code base. They are maintained on Github by Matthew D. Green of Johns Hopkins for teaching and research purposes.
Tornado Cash and Tornado Nova are open-source coin mixing tools that were developed by an independent team of software developers and deployed onto Ethereum and several other blockchains. On August 8, 2022 the Office of Foreign Assets Control (OFAC), a division of the US Treasury, declared "Tornado Cash" and "Tornado Cash Nova" to be Specially Designated Nationals (SDNs): the result was to effectively sanction the Tornado Cash organization, its software development repositories, and the main smart contract deployment on Ethereum.
This move to sanction Tornado Cash represents the first instance in which the US government has applied economic sanctions to an open source software project. As a result of this announcement, several cryptocurrency exchanges have banned users who interact with the Tornado Cash smart contract address on Ethereum. Within hours of the OFAC announcement, Github shut down the user accounts of all known Tornado Cash developers and removed the source code repositories owned by Tornado's Github organization.
While Github succeeded in removing the original copies of all Tornado source code repositories, they did not remove all "forks" of the code made by GitHub users. Several of these forks were recently collected and (further) forked by contributors to the tornadocash-community organization. Those folks did the hard work. The current repository is simply another fork of the repositories they collected.
If you want a copy of the code on a more durable decentralized medium, there are copies of (limited) repositories on IPFS. I certainly don't warranty these (or any of this code), and you should carefully check hashes against the repositories on Github and in the Wayback Machine just in case:
- Tornado Nova:
ipfs://bafybeiho72nozeq2mi6egptem77omhujt5ovpx4jjskg5sz2ti57zlunmm - Tornado Cash Classic:
ipfs://bafybeicu2anhh7cxbeeakzqjfy3pisok2nakyiemm3jxd66ng35ib6y5ri
- Tornado Nova:
- Daniel Bernstein announced second lawsuit against the U.S. government
cross-posted from: https://community.hackliberty.org/post/309
- Understanding RSAgit.hackliberty.org Works/understanding-rsa.md at main
Works - Just a collection of works I have done to help and educate others on a range of topics

cross-posted from: https://community.hackliberty.org/post/18
> I put together a short paper on understanding the underlying mathematics of RSA encryption. I hope it helps others to understand what is happening at a fundamental level with RSA
- SafeCurves: choosing safe curves for elliptic-curve cryptography
cross-posted from: https://community.hackliberty.org/post/17
- Post-Quantum VPN Tunnelsmullvad.net Post-quantum safe VPN tunnels available on all WireGuard servers | Mullvad VPN
The experimental quantum-resistant tunnel support we posted about in July is now available on all our WireGuard servers! We also upgraded the protocol to allow even more secure key exchanges in the future.

cross-posted from: https://community.hackliberty.org/post/25302
- Guidance for Choosing an Elliptic Curve Signature Algorithm in 2022soatok.blog Guidance for Choosing an Elliptic Curve Signature Algorithm in 2022 - Dhole Moments
A cartoon wild canid on the Internet provides general guidance on elliptic curve cryptography parameter choices.

cross-posted from: https://community.hackliberty.org/post/20087
Earlier this year, Cendyne published A Deep Dive into Ed25519 Signatures, which covered some of the different types of digital signature algorithms, but mostly delved into the Ed25519 algorithm. Truth in advertising.
This got me thinking, “Why isn’t there a better comparison of different elliptic curve signature algorithms available online?”
Most people just defer to SafeCurves, but it’s a little dated: We have complete addition formulas for Weierstrass curves now, but SafeCurves doesn’t reflect that.
For the purpose of simplicity, I’m not going to focus on a general treatment of Elliptic Curve Cryptography (ECC), which includes pairing-based cryptography, Elliptic-Curve Diffie-Hellman, and (arguably) isogeny cryptography.
Instead, I’m going to focus entirely on elliptic curve digital signature algorithms.
- How to set up "always encrypted" Rocket.Chat on Kubernetes (Constellation)dev.to How to set up "always encrypted" Rocket.Chat🚀 on Kubernetes
I recently posted about the open-source release of our "always encrypted" K8s distro Constellation....

cross-posted from: https://community.hackliberty.org/post/12439
This post is about running Rocket.Chat on Constellation, which gives, well, "always encrypted" Rocket.Chat 🙂
This is cool, because "always encrypted" Rocket.Chat shields the entire server-side of Rocket.Chat from the (cloud) infrastructure and ensures that all data is always encrypted - even during processing in memory.
- Join the discussion about Internet Censorship Circumventiongithub.com GitHub - net4people/bbs: Forum for discussing Internet censorship circumvention
Forum for discussing Internet censorship circumvention - GitHub - net4people/bbs: Forum for discussing Internet censorship circumvention

cross-posted from: https://community.hackliberty.org/post/10450
Join the discussion at GitHub - net4people/bbs
- Run your own Numbers Station
cross-posted from: https://community.hackliberty.org/post/8851
- Cryptanalysis proves Mega.nz crypto architecture "riddled with fundamental cryptography flaws"arstechnica.com Mega says it can’t decrypt your files. New POC exploit shows otherwise
Fundamental flaws uncovered in Mega's encryption scheme show service can read your data.

cross-posted from: https://links.hackliberty.org/post/136
> cross-posted from: https://community.hackliberty.org/post/77 > > An entity controlling MEGA’s core infrastructure can tamper with the encrypted RSA private key and deceive the client into leaking information about one of the prime factors of the RSA modulus during the session ID exchange. More specifically, the session ID that the client decrypts with the mauled private key and sends to the server will reveal whether the prime is smaller or greater than an adversarially chosen value. This information enables a binary search for the prime factor, with one comparison per client login attempt, allowing the adversary to recover the private RSA key after 1023 client logins. Using lattice cryptanalysis, the number of login attempts required for the attack can be reduced to 512.
