
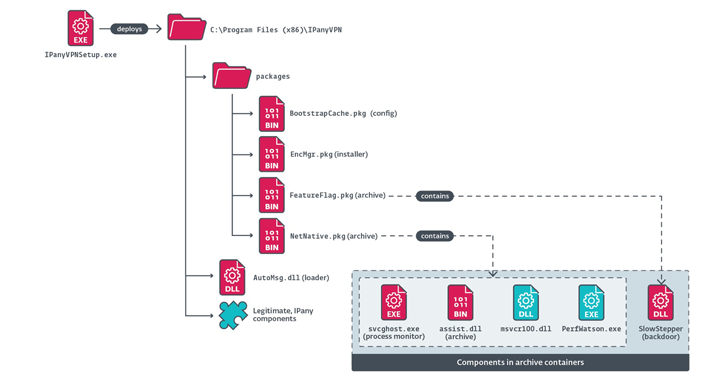
PlushDaemon APT targets South Korean VPN with SlowStepper backdoor. Multistage DNS C&C protocol aids espionage.



Welcome to the first operations security (OPSEC) community on Lemmy!
This is a space dedicated to discussing, sharing, and learning about operational security practices. Whether you are a business owner, a cybersecurity expert, or just a regular person, you can always benefit from a little extra OPSEC in your life.
As we belong to Lemmy.zip all of their guidelines apply on top of ours.
PlushDaemon APT Targets South Korean VPN Provider in Supply Chain Attack

PlushDaemon APT targets South Korean VPN with SlowStepper backdoor. Multistage DNS C&C protocol aids espionage.

Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platforms

Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform - research.md

Europol chief calls on tech giants to unlock encrypted messages

The chief of Europol chief has urged technology companies to cooperate with law enforcement in unlocking encrypted messages. A failure to do so...

The Europol chief said that in a digital environment, the police needed to be able to decode these messages to fight crime. “You will not be able to enforce democracy without it,” she added.
"Anonymity is not a fundamental right,” she told the Financial Times.
PSA: RUN YOUR OWN MONERO NODE
Click to view this content.
A leaked video from Chainalysis has shown they have delivered on the IRS's $1.25 million contract to trace Monero.
The good news is that their tracking heavily relies on you connecting to a compromised node.
The (debatably) bad news is that you need to run your own node to ensure privacy.
Review the linked video from Mental Outlaw (I love that guy) for more information.
BusKill (Dead Man Switch) Warrant Canary for 2025 H1

This post contains the cryptographically-signed BusKill warrant canary #007 for January 2025 to June 2025.

This post contains a canary message that's cryptographically signed by the official BusKill PGP release key
 |
|---|
| The BusKill project just published their Warrant Canary #009 |
For more information about BusKill canaries, see:
undefined
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA512 Status: All good Release: 2025-01-14 Period: 2025-01-01 to 2025-06-01 Expiry: 2025-06-30 Statements ========== The BusKill Team who have digitally signed this file [1] state the following: 1. The date of issue of this canary is January 14, 2025. 2. The current BusKill Signing Key (2020.07) is E0AF FF57 DC00 FBE0 5635 8761 4AE2 1E19 36CE 786A 3. We
While it can be a hassle, reducing your attack surface is always recommended


Even though Bluetooth is designed to be secure, vulnerabilities can sneak in. We saw an example of that with the Flipper Zero being able to spam Apple devices, and while that was relatively harmless, that doesn't mean the next vulnerability will be.
Copypastas are now allowed
Well, you guys won. Copypastas are now allowed as comments if they are related to the post or parent comment. However, they still can't be posts.
Rule 3 has been updated.
As much as I would not prefer this, we are a community and not a monarchy.
Good resources to monitor cybersecurity?
One site I've been following for awhile is https://notifycyber.com/
...but I'd love some more. What are your must-haves?